The article deals with modern web application security risks and methods of their prevention. Based on the analysis of modern literature, the author systematizes key threats to web application, presents a brief description of the main ones and highlights promising prevention and elimination measures.
Keywords: web application, attack, risk, injection, coding.
Nowadays, the role of the Internet for the software environment has increased significantly. Applications created using Web technologies have become the best solution for various industries and have gradually displaced applications based on other technologies. This has led to the complexity of Web applications in terms of structure, architecture, and implementation. In addition, distributed architecture has gained wide adoption. This state of affairs has put forward new demands on Web application security issues.
Every year, attackers develop increasingly sophisticated methods of attacking Web applications to compromise sensitive information and gain access to databases. Accordingly, security experts consider exploited vulnerabilities and strengthen their systems based on the knowledge gained. However, the aggregate frequency and cost of data leaks is increasing in geometric progression, and as of today, it is around US$9.17 million. According to expert reports, 96 % of Web applications have defects and anomalies [1].
According to the latest DBIR study, Web applications are the primary attack vector in 2024, projected to be used by attackers in 80 % of incidents. Web applications are prime targets for attacks for two reasons. First, many of them contain vulnerabilities or configuration errors. Second, a significant portion of Web applications store extremely valuable information, such as personal and financial data, and in the event of a successful hack, attackers will gain direct access to this data. A study by Kaspersky found that 40 % of IT professionals engaged in ethical hacking consider Web application attacks to be among the most profitable for cybercriminals, and 55 % claim the same for APIs [2].
Overall, the data provided confirm that Web application attacks remain the biggest and most serious security threat on the Internet and require constant monitoring and security measures, which has predetermined the choice of the topic of this article.
The basic principles of Web application security, including, issues such as threat identification, attack protection, interception protection, and data tampering are addressed in their papers by N. N. Teterin, T. P. Semenov, A. K. Blagorazumov, P. E. Chernikov, G. E. Glukhov, A. V. Semin.
An extensive overview of the vulnerabilities that are specific to Web applications, including data entry-level attacks, session security risks, and server attacks, is presented in the publications of G. S. Ermakova, N. N. Panteleeva, T. V. Azarnova, P. V. Polukhina, V. A. Prytkova.
At the same time, despite the significant number of publications on the research topic, the emergence of new protocols and standards, and the capabilities of artificial intelligence technologies, the substantial growth of malicious traffic activity on the Internet necessitates the need to constantly update and actualize the conclusions and recommendations in this subject area.
Thus, the purpose of the paper is to study the current threats and ways to ensure the security of Web applications.
First and foremost, it is essential to note that Web application security is the practice of detecting and preventing cyberattacks on them and, more importantly, creating applications that are initially secure. This includes a set of security controls embedded in Web applications to protect against a growing number of cyberthreats [3].
Based on a study of Web application incidents detected and remediated in December 2023, experts identified the following facts:
— 30 % of all web application attacks targeted security system misconfiguration — for example, coding and implementation errors;
— 21 % of attacks involved code injections. These weren’t just SQL injections (typically designed to steal, destroy, or manipulate data). Attacks using LDAP and Log4Shell have also been popular [4].
Based on the literature available to date, using research results and data from analytical reports, in Figs. 1 author highlights the most common current threats to Web application security.
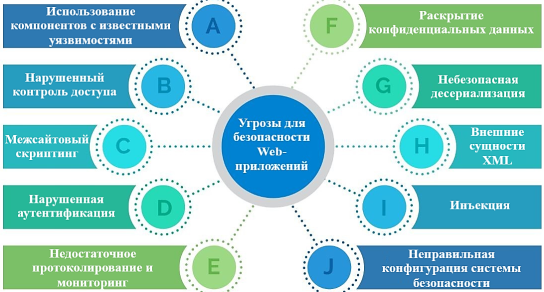
Fig. 1 Major Web Application Security Threats
It is not possible to consider all threats within the scope of this article, so we will briefly characterize some of them with a special focus on ways to prevent them.
Injection attacks . A web application vulnerable to intrusion attacks accepts untrusted data from an input field without properly preprocessing it. By embedding code in the input field, an attacker can trick the server, causing it to interpret the code as a system command and thus implement the attack.
Common injection attacks include SQL injections, cross-site scripting, email header injections, and more. These attacks can result in unauthorized access to databases and the use of administrator privileges.
To prevent injection attacks, the following measures are important:
— disallowing unreliable command and query inputs;
— using a secure application programming interface that bypasses interpreters or applies parameterized interfaces;
— filtering and decontaminating all input data according to the whitelist.
Improper Security Configuration . The most frequent and usual threats to Web applications arise due to improper configuration. They become possible as a result of inadequate or insecure system settings, the use of public cloud repositories, or cryptographic error alerts. To prevent misconfiguration, all operating systems, frameworks, libraries, and applications must be securely configured, patched, and conform to best practices recommended by the hardware or software manufacturer.
Violated authentication. This is a general threat term referring to vulnerabilities in which authentication and session management tokens are inadequately implemented. Compromised authentication allows hackers to claim the identity of a legitimate user, access their confidential data, and potentially exploit assigned identity privileges. To prevent and prevent this threat, you should terminate sessions after a certain period of inactivity, revoke the session ID immediately after it ends, set limits on password simplicity, and implement multi-factor authentication.
Unsafe Deserialization. This threat often leads to remote code execution situations. These flaws allow replay, injection, and privilege escalation attacks to be conducted even if remote code execution does not occur. Banning calibrated objects from unreliable sources is one way to prevent this kind of threat.
Cross-site scripting. Cross-site scripting attacks imply the injection of malicious code or a malicious script into a Web application. The application then executes the script, allowing the attacker to steal sensitive user data, such as session tokens and cookies, or perform other actions. If successful, a cross-site scripting attack can result in the theft of user session IDs, corruption of the Web application, and redirection to malicious sites, enabling phishing attacks.
The following actions must be taken to level this threat:
- Verification of user-entered data.
- Using inference coding techniques.
- Application of car sanitation libraries such as OWASP AntiSamy.
- Implement a content security policy.
Thus, in summary, note that Web applications are attractive attack vectors for cybercriminals, and today they are subjected to increasingly frequent illegal impacts. In order to ensure the security of the Web application, it is advisable to use the latest tools to scan and monitor for vulnerabilities and threats, and to apply the latest secure coding techniques.
References:
- Rusakov A. M. Development of web application reliability analyzer based on network attack simulation // Modern science: current issues of theory and practice. 2023. No 7–2. S. 105–112.
- Belyaeva K. V. Web Development Security: HTTPS, CORS, XSS, CSRF, CSP // International Journal of Information Technology and Energy Efficiency. 2023. Vol. 8. No 5–2 (31). S. 83–85.
- Gumbina E. A. Principles and mechanisms of data security in web applications // Current research. 2024. No 6–1. S. 62–66.
- Chavez K. G. Applications of Machine Learning in Software Development to Prevent CSRF Vulnerabilities in Web Applications // Modern Science: Current Issues of Theory and Practice. Series: Natural and technical sciences. 2023. No 9–2. S. 127–132.

