This article is proposed guidelines testing, allow to get the evaluation of performance/failure of Intrusion detection systems fixed set of functions defined by any settings, as well as assessing the vulnerability of these funds. Intrusion detection systems is deployed and configured to meet the requirements of operational documents and security policy of the organization operating Intrusion detection systems.
1 Introduction
Network intrusion detection systems and detect signs of attacks against information systems have long been used as one of the essential lines of defense information systems. The developer system protection information systems and consultants in this area is actively used such concepts as perimeter security, stationary and dynamic defense, began to appear own terms, for example, proactive protection. Intrusion detection systems and attacks are usually a software or hardware-software solutions that automate the process of monitoring events occurring in a computer system or network, as well as independently analyze these developments in the search for signs of security problems. As the number different types and ways of organizing unauthorized intrusion into other people's network in recent years has increased significantly, intrusion detection systems (IDS) have become an essential component of the security infrastructure of most organizations [1]. This contributes to a huge amount of literature on the subject that potential attackers are carefully studying and increasingly sophisticated and complex methods and approaches to the detection of hacking attempts of information systems.
Nowadays on the market are a large number of commercial intrusion detection systems. However, until now there is no standardized method of testing, allowing to identify the pros and cons of IDS test. The tests recommended by the manufacturer, as a rule, serve advertising purposes and cannot help to evaluate the functionality of the system.
2 The evaluation criteria for the functional test
Intrusion Detection — the ability of IDS to detect different types of attacks based on the analysis of various parts of a packet. We should consider the following basic characteristics of IDS:
Ability to analyze the headlines — allow to detection attacks associated with the values of IP-packet header. A typical representative is LAND-attack. LAND-attack sends a SYN packet with the same values IP- addresses and source and destination ports. Machine receiver gets into an infinite loop, which can cause the collapse of the network.
Collect packets — the ability IDS to collection fragmented traffic and detect attacks, prisoners in several batches. A typical representative is Tear Drop-attack. This attack is initiated by sending a number of IP-packets that after assembly have overlapping data packets. This can cause instability in the operation of the network or system.
Analysis of the data packet — allows IDS detect attacks associated with the data packets [2]. A typical representative of such an attack is called PHF-attack on HTTP. CGI-program of PHF is an example of a script that you can use to work with the address book and to exploit the vulnerability allows locally run any command.
It is also necessary to take into account the following criteria:
- The ability IDS defines IP Dsync — intrusion detection, in which the purpose of masking the non-standard values are given sequence numbers and size.
- The ability IDS detects distributed attacks — identified characteristics of IDS, using the correlation method to detect attacks, distributed in time or in space (the attack is carried out with multiple hosts with different IP-addresses).
- The ability to save information for analysis — characterizes the capabilities of the program for the conservation of incidents for further analysis.
- The presence of a distributed architecture — a very important feature for IDS that are used in large networks. This test determines the architecture of IDS and shows the ability of the console with multiple sensors.
- The architecture of the system of decision-making — shows where the final decision about the discovery of attack — on the sensor or on the control console.
- Bandwidth — allows you to assess the ability IDS to capture packets, without causing them loss. For this test, we used only the pure traffic not containing attacks.
- The impact on system performance — a test to evaluate the impact IDS on the work load of the CPU and memory and also the overall performance of the host.
Checking IDS is done by simulating attacks or anomalous activities. At the same time for the successful completion of checks, signature-based IDS must present signatures for each of the produced action. If these signatures are missing, they must be created manually in the preparation and setting up IDS testing. Topology stand for testing is shown in figure 1.
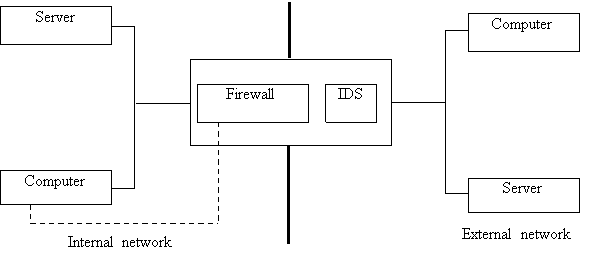
Fig.1. Scheme stand for testing
Each test is the introduction of special packets to the network, which operates the system under test intrusion detection. Test results can be tracked on the management console system. Tests are universal, they are perceived test IDS as a «black box». All tests used the protocol TCP. In most cases, the tests used embedded interaction between the packets and the third party — the so-called «target» host subjected to «attack».
This host is the purpose of the appointment of all test packets. The presence of such a «target» host allows you to simulate «real». For this purpose is serve emulator network services. Moreover, target host also plays the role of checking the efficiency of the experiment [3]. His reaction to the embedded packet allows you to monitor the behavior of «real» TCP-connection and compare it with information on the behavior displayed on the control console test IDS. In each test the network with software host-load generator is modeled such traffic that might occur during normal operation of the network.
Packets, introduced in traffic, are slightly different for each test. Tested IDS responds to every test detection or intrusion detection. Analyzing posts IDS and type of packets used in the particular test, it can conclude about the possibilities and characteristics of IDS test. Before you carry out comprehensive, special tests should be carried out a series of tests the basic functions of IDS. On the target host for visualize network activity using a packet sniffer. By controlling this activity, you can say whether or not the tested IDS generally detect simulated attack.
3 Performance testing. The objectives of performance testing
Performance tests are conducted in an environment where the attacker, the victim and the COA are located in the same network [4–5]. In this case, the tests do not interfere with the device for limiting the bandwidth. The purpose of the performance tests is determined the characteristics of working IDS with packet. Figure 2 illustrates stand topology for such tests.
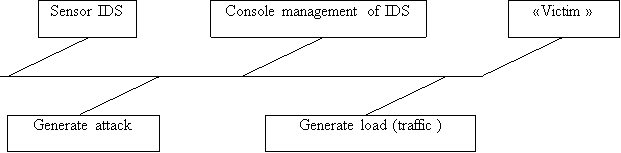
Fig.2. Stand topology for performance tests
4 The evaluation criteria for the performance tests
Criteria for assessing the performance of the following:
- Bandwidth — allows you to assess the ability of IDS to capture packets, without causing them loss.
- Builds — a test to determine the performance of the sensor when assembling packets.
- Filtration efficiency — a test designed to assess the overall effectiveness of the system in solving the problem of interception, packet analysis and response to the attack.
- The impact on system performance — a test to evaluate the impact work IDS on the load of the CPU and memory and the overall performance of the host.
5 Conclusions
In conclusion we can say that the proposed guidelines define the evaluation criteria for functionalIDS tests based on the analysis of various parts packets and responds to every test detection or intrusion detection in computer networks.
References:
- S. Mandujano, A. Galv6n, J. A. Nolazco. An Ontology-based Multiagent Architecture for Outbound Intrusion Detection // Proc. 3rd ACS/IEEE International Conference on Computer Systems and Applications, 2005. — C. 94–101.
- Li Muh., Li Min., and Jiang X.DDoS attacks detection model and its application // WSEAS Trans. Computers. 2008. V.7. No. 8.P.1159–1168.
- Kim J., Bentley P. An artificial immune model for network intrusion detection: http://neuro.bstu.by/our/immune3.pdf, 20.10.2011.
- Kotov V., Vasilyev V. Immune approach to network intrusion detection // Proc. of Security of Information and Networks. 2010. P. 233–237.
- Scarfone, Karen; Mell, Peter (February 2007). «Guide to Intrusion Detection and Prevention Systems (IDPS)» (PDF). Computer Security Resource Center (National Institute of Standards and Technology) (800–94). Retrieved 1 January 2010.

