This study aims to look into the causes and solutions of quid pro quo attacks, which are a major problem of data loss and financial loss among Kazakh citizens. Early acquisition of cyber security and digital literacy can therefore be beneficial in all spheres of life. In order to estimate the problem's issue, its causes, and potential solutions, the study used a quantitative method of data collection called a survey. The majority of Kazakhstanis, according to the results, are unaware of quid pro quo or social engineering attacks. The study's conclusions may be useful for designing educational initiatives as well as for future investigation into substitute strategies for stopping quid pro quo social engineering attacks.
Keywords: social engineering, cybersecurity, digital literacy, quid pro quo.
Целью данного исследования является изучение причин и путей решения атак типа «кви про кво», которые являются основной проблемой потери данных и финансовых потерь среди граждан Казахстана. Таким образом, раннее приобретение знаний в области кибербезопасности и цифровой грамотности может быть полезным во всех сферах жизни. Чтобы оценить суть проблемы, ее причины и возможные пути решения, в исследовании использовался количественный метод сбора данных, называемый опросом. Согласно результатам, большинство казахстанцев не знают об “кви про кво” или других атаках социальной инженерии. Выводы исследования могут быть полезны для разработки образовательных инициатив, а также для будущих исследований альтернативных стратегий предотвращения атак социальной инженерии «кви про кво».
Ключевые слова: социальная инженерия, кибербезопасность, цифровая грамотность, услуга за услугу.
Introduction
Today, people across the world are concerned about cybersecurity, making it more than just a problem for big businesses and governments. The ways that malevolent actors use to take advantage of weaknesses and compromise private and sensitive data are developing along with technology. Ensuring the security of sensitive and personal data is crucial in the modern connected world where digital interactions are ubiquitous. Social engineering attacks can have a variety of negative effects, such as identity theft, money loss, reputational harm, and even threats to national security. Therefore, protecting people, organizations, and society at large requires an understanding of how to effectively counter such threats. So, researching the topic of raising cybersecurity awareness to prevent quid pro quo social engineering is important for reasons that go far beyond scholarly interest. Quid pro quo is a strategy whereby attackers coerce victims into disclosing private information or acting against their better judgment in return for benefits that are promised. The first appearance of quid pro quo social engineering attack was in 1184 B.C during Trojan war. The Greeks and Trojans were engaged in a protracted conflict that seemed to never end. Following a ten-year siege, the Greeks realized they would need to use cunning to overcome the Trojans. They built a massive wooden horse and used it to conceal part of their army. Seemingly defeated, the remaining military personnel sailed away. The wooden statue was dragged past the Trojans' defenses as a trophy for their long-overdue victory, and they fell for the trick. The Greek soldiers inside the horse crept out after the sun set and the Trojans went to bed, opening the city's gates to let the rest of their armed forces, who had sailed back under cover of darkness, in. Afterwards, the Greeks employed the element of surprise to destroy city the city from inside, formally ending the war. That is the first documented case of social engineering. Even though deception was practiced by almost all of civilized humanity, it wasn't until millennia later that this kind of deception was given a name. It was more deliberate and methodical than a mere ruse, involving deliberate actions planned out to manipulate and breach a barrier. Then, it popularized within development of communication technology in 1990s. In Kazakhstan quid pro quo attack started nearly in 2000, due to the recent independence of Kazakhstan (Mitnick Security Consulting, n.d.). An exchange of «give and take» characterizes a quid pro quo attack. It has a literal meaning for something. Because of the law of psychological reciprocity, which governs human behavior, this idea of exchange is essential. This implies that we feel obligated to repay someone for anything they give us or do for us. When quid pro quo is involved, the benefit or advantage that is promised in return for information is typically in the form of a service (if it takes the form of a good, it is considered a baiting attack) (Nadeem, 2023). Over 37 million fraudulent calls from overseas to Kazakhstan were stopped by the Kazakh police, the Ministry of Digital Development, and telecom companies in 2023. According to official reports, this was discussed at a briefing held at the Ministry of Internal Affairs. The Ministry of Internal Affairs stated at the end of October of that year that 13 billion tenge had been lost to Kazakhstanis because of remote scammers. There have been 1,600 reported instances of fraudulent online loans made through banks and microlending institutions (Ruzmatova, 2023).
I selected this topic (interest) because I'm interested in cyber security and want to work in it and because many of my friends and family members experienced quid pro quo social engineering, this issue took on real significance and relevance for me. Furthermore, I want to support my nation and its citizens in avoiding problems and in achieving the 9th Sustainable Development Goal, which is Industry, Innovation, and Infrastructure.
Aims
The primary purpose of my research is to help people, to be more precisely, help to prevent quid pro quo attacks among people in Kazakhstan and teach them how to be aware of it and how to make yourself secure from such cyber security attacks.
- Questions:
- Which awareness-raising and educational programs enable Kazakhstanis to identify and reject quid pro quo social engineering strategies the most effectively?
- What are the most targeted parts of society and government of quid pro quo attack?
- What are the factors of increased number of quid pro quo social engineering attacks in Kazakhstan?
These questions will assist me to find and understand the nature of the issue and will help my logic and me to solve it in the most efficient and simple way.
Literature Review
Issue:
With technology advancing at a breakneck speed and connected digital environments defining our age, cybersecurity is more important than ever. The vulnerabilities to cyber threats have increased dramatically as we use the internet to navigate its vast reaches, transact business, and share information at a rate never seen before. It is generally known and observed that most cyberattacks happen by using human factors, in other words, social engineering. To begin with, cybersecurity is a process of protecting any data, computer services, and systems from loss or hack (Craigen, 2014). Social engineering is a type of cyberattack that uses human manipulation techniques, which exploits the human factor and uses human interactions to obtain access to some data (Raza, 2023). One type of social engineering attack known as «quid pro quo» occurs when a hacker offers financial gain in return for information that can be used to steal money, data, or even take over a website user's account. (Nadeem, 2023). It is well known that 98 % of all cyberattacks involve social engineering in one way or another. Recently, 43 % of cyber-attacks on small businesses were done by using social engineering techniques, which include quid pro quo attacks. Additionally, in higher education, there were observed that 41 % of cybersecurity attacks used social engineering (Purplesec, 2023). So, is there any way to find a solution to the issue? According to Dara Security and Emily Miller's article, the solutions are training people on an appropriate response, being aware of quid pro quo attacks, and involving and informing other people, in other words developing their critical thinking skills.
The attack might entail posing as a reputable person to persuade a worker to click on a malicious email or link, feigning to be a trustworthy bank to obtain login information, or engaging in other similar actions meant to obtain access to target systems. The «quid pro quo» social engineering tactic relies on the perpetrator's capacity to lure victims in with a complimentary good or service. Quid Pro Quo, which means «this for that», is a well-known social engineering con that preys on people's credulity to acquire personal data.. For example, the attacker may pose as an IT support specialist and call all internal direct lines of a company in an attempt to locate a legitimate IT support user. Once this user is located, the attacker will “assist” in resolving the IT issue. The victim voluntarily provides the attacker with sensitive information, believing that the attacker needs network access credentials in order to resolve the IT issue (Dara Security, 2015).
Firstly, one of the solutions is training employees and others to recognize such social engineering attacks and always think properly during their labor. In addition, for organizations and companies, sensitive information should never be shared by an employee unless they start the conversation. Employees would be advised to return the call, if it was made by an outside caller, using the number listed on the caller's business website. For example, during any social engineering attack, a calm person with nice critical thinking will consider the situation carefully and do exactly, according to his work rules or his logic, that is finding out the caller is a fraud or an official employee of a company (Miller, 2023). So, the best way to prevent quid pro quo attacks is by training and informing people about the problem. For instance, try some training lessons, send information, and do posters about how social engineering is done and how to avoid it (Dara Security, 2015).
Secondly, the other solution is involving other people in the situation. During a quid pro quo attack, some people may not be able to remain calm and confident, and this may lead to a leak of secure data. Every person may have critical thinking, but some of them may not use it in dangerous situations. If a person is unsure about a situation and may not remember training information on your own, he or she is to talk to a trusted friend or family member. Often, a single conversation can spread awareness of an existing scam. After that, people who have been under a quid pro quo attack should report the attack to authorities or reputable organizations. By reporting scams, people may spread awareness of evolving attacks among other people. Updating security software, creating databases of well-known frauds, and apprehending the perpetrators of these assaults can all be accomplished with the help of this knowledge. For example, in 2022, there were over twice as many reports of work scams to the Federal Trade Commission (FTC) as there were in 2020. In the first quarter of 2022, job scams defrauded Americans of $68 million (Miller, 2023). And in 2023 alone, approximately 5701 quid pro quo attack calls were done in Kazakhstan (Maulenkulov, 2023).
In conclusion, proactive and cooperative measures are required to counter the growing threat of cyberattacks, especially those that involve social engineering techniques like quid pro quo. Strong training programs are essential because they enable people to identify and thwart social engineering schemes by using increased awareness and critical thinking. Establishing a culture of caution is crucial, with a focus on the idea that private information should only be disclosed at the request of the individual. Involving others in the process also strengthens group cybersecurity efforts by establishing a helpful network for advice-giving and experience-sharing. Reporting suspected attacks promptly helps the battle against cyber threats by providing important data. As the digital landscape changes, maintaining a secure environment where people are treated as robust defense mechanisms rather than as vulnerabilities requires constant education, awareness campaigns, and cooperative vigilance.
Methodology
The collection of information about the problem was a crucial component of the present research. In the research, quantitative data collection method was chosen and used, one of which is a survey, to find the trends and comprehend relationships, patterns, and phenomena. In this instance, the data presented consists of numerical information, such as the number of participants who received fraud calls, percentages representing participants' opinions, and response frequencies. The ability of quantitative data to yield unbiased, trustworthy, and broadly applicable results is one of its key benefits. Rigid and standardized techniques, like computer software, statistical testing, and mathematical formulas, can be used to analyze quantitative data. As a result, there is less chance of subjectivity, bias, or error in the gathering and analysis of the data (What Are Some of the Advantages and Disadvantages of Using Quantitative and Qualitative Data?, 2023). Analyzing secondary sources of information on the Internet was crucial because broad overview and comprehension of the issue was needed. Surveys and interviews are less biased and easier to administer than experimental data gathering methods because multiple perspectives are considered rather than just mine.
Firstly, for secondary source of information there has been done literature review on several papers on the similar topics. Most of them were research information directories and guides (Dara Security, PurpleSec), written in the past and various countries. Local sources, like Nur.kz and Orda.kz, provided information about the issue in our country. Based on citizen observations, small information agencies presented a range of issues with fraud calls and partial statistical information in Kazakhstan, which were considered as trustworthy and believable sources. Regretfully, on Kazakhstan's government platform or any other online sources, it was impossible to find any documents and papers that contained precise cases about the social engineering attacks happening in the society.
The purpose of the survey was to gather the perspectives of Kazakhstan's various social groups. By this survey questionnaire, as an instrument tool, people’s perspectives and thoughts were observed to generalize results for a big number of respondents (Creswell, 2001). For all participants, the online anonymous questionnaire was divided into two main question sections. People proceeded with the survey and moved on to the next page of the main questions based on their responses to the first section of questions. As a result, participants were asked to check options in the first section indicating their consent to share their personal thoughts and viewpoints on the subject for research. Then, after giving an agreement to pass the survey, people were required to several questions about the problem of ‘quid pro quo’ attacks in Kazakhstan. Some of the questions asked people an information about their age, gender, and experience of having or witnessing the issue at least one in their lives. In addition, there were other questions asking people’s opinion of several problem aspects: ways of solving, frequency of having or witnessing, reasons and factors of the problem.
The chosen sample for the methods mentioned was — citizens of Kazakhstan since it is primary reason to help my nation and people to avoid such problems and instead of considering only one particular region all citizens of the country were chosen because of popularity, relevance, and prevalence of the issue. The end goal of this study was to find the main factor in increasing the number of 'quid pro quo' social engineering attacks in Kazakhstan. The explicit respondents were not chosen with any parameters, because their availability was not predictable at that time.
However, most respondents were teenagers and young adults, which is not a sufficiently high-quality audience.
It is important to be aware of these techniques' limitations, though. Conclusions may not be generalized because the survey only represent a small portion of our country’s citizens with different statistical properties (there are 20 million people in Kazakhstan and women make up most of the population), however the survey has enough confidence level and margin of error to overcome this limitation, 95 % and 6.8 % respectively. Furthermore, there were a lot of cases when responds were in lack; it was difficult to collect information from auditory and to mitigate this difficulty, a link for the survey were distributed almost to all country regions. Finally, it is believed that funding for this kind of general research and data collection should come from both the government and communication companies. As a result, the public might start showing genuine interest in helping with data collection.
Results
The problem was generally understood by using secondary sources of data, which were beneficial, useful, and helpful. Nevertheless, primary sources such as a survey provided far more valuable information for this research project. As a matter of fact, this primary source assisted in finding the reasons for the widely common quid pro quo attacks in Kazakhstan and solutions for preventing and protecting citizens from them. Each survey respondent expressed their awareness and understanding of the issue by sharing their own opinions. Though the opinions differ greatly from one another, there are some fundamental concepts that are shared by all.
208 individuals in total took part in the multiple-choice online survey that was distributed to academic staff, students at NIS Aktobe via Outlook and public, and simple citizens by messengers like messengers like WhatsApp, TikTok, Discord, VKontakte, Telegram, and Instagram. There were 81 women (38.9 %) and 128 men (61.5 %) ( Figure-1 ). The purpose of the questionnaire was to identify citizen’s perspectives and personal views about social engineering techniques used in cybersecurity attacks by methods below.
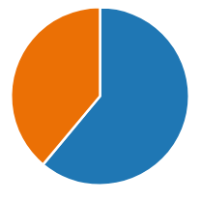
Fig. 1. Male and female pie chart: blue — male (128), orange — female (81)
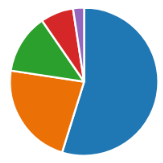
Fig. 2. Age group pie chart: blue: 11–17 (114), orange: 18–25 (47), green: 26–40 (27), red: 41–59 (15), purple: 60+ (5)
Firstly, the respondents were divided by age and gender groups and whether they were victims or witnesses of social engineering attacks or not. The fact that nearly half of the participants —40 %—responded that they had either experienced or witnessed quid pro quo attacks indicates how relevant the issue is. Additional questions were defined by the second criterion ( Figure-3 ).
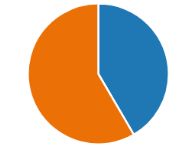
Fig. 3. People who were a victim or witness of social engineering attacks: orange: Yes (84), blue: No (124)
Those with any connection to quid pro quo attacks were invited to discuss their user experiences and highlight pertinent issues with specific routes. Participants first estimated their knowledge and skills in the cybersecurity field. As expected, more than a quarter of the respondents consider their knowledge as an average and only 21.6 % of participants claim that they have high degree skills in that field. What's more intriguing is that 18 respondents said they didn't know anything about social engineering or cybersecurity. The similar phenomenon is seen in the research results provided by Forbes.kz in 2022 where small proportion (13 %) of all participants were not aware of cybersecurity. ( Figure-4 ).
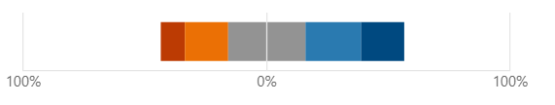
Fig. 4. Rate of people about their knowledge about cyber security and social engineering:
red: very low (8.7 %)
orange: low (13.9 %)
grey: average (31.3 %)
light blue: high (24.5 %)
blue: very high (21.6 %)
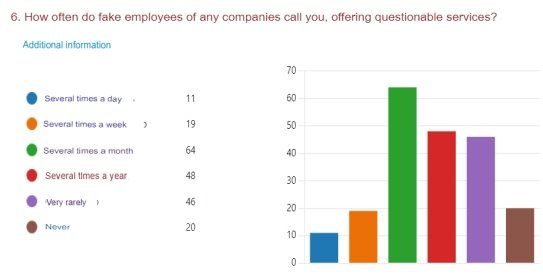
Fig. 5. Frequency of fake calls to Kazakhstani people
According to the data obtained by the survey quid pro quo attacks among citizens occur multiple times per month and it is more frequently than the average, which is 1 call in 2 months (Forbes.kz, 2024). In addition, it is important to note that the majority of participants indicated that older people were the age group most impacted by the attacks and that the prevalence of the issue is related to the unawareness of people, especially elderly citizens. These figures unequivocally demonstrate that the issue is most prevalent among seniors ( Figure-6 ).

Fig. 6. The most influenced social group according to people’s opinions
Stricter fraud laws (72.7 %), teaching digital literacy (82.7 %), and critical thinking instruction (73.6 % of respondents) are the main strategies that help stop quid pro quo social engineering attacks among Kazakhs, according to survey participants’ opinion. However, some of the respondents (16.3 %) considered the method of stricter fraud laws as a solution with the least impact on solving the problem ( Figure-7 ).
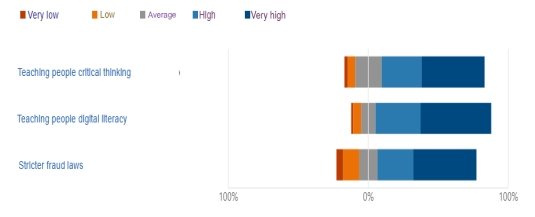
Fig. 7. Influence of the factor to the problem according to people’s opinions
Numerous solutions have been put forth to address the issue of broadly dispersed quid pro quo attacks. Some were straightforward, such as «find new ways of tracing scammers and frauds, then punish them» or “spreading information about the attacks in mass media of the country” (as expressed in the majority opinion), but others were far more intricate, demonstrating the genuine concern that people have for the problem. Some participants proposed, for example, that a course on quid pro quo attacks be added to the curriculum. Others proposed using media, including movies, cartoons, podcasts, and videos, to convey educational content in an engaging way, emphasizing the significance of finding solutions to the problem. In addition, some participants suggested adding a special education program just for elderly people as they are the most influenced age group.
Conclusion
The purpose of this research was to investigate reasons and solutions of the quid pro quo social engineering attacks problem in Kazakhstan. The answer to the research question implies changes in education system by including some courses aimed to educate people to recognize and prevent potential quid pro quo attacks.
At the beginning of the research, the majority views and possible reasons were shared about the problems of quid pro quo attacks and their reasons, and eventually it was contributed to prove them all by doing this research. However, it was found that there are some interesting and creative ways of solving the issue, such as educating people to avoid the problem by media (cartoon, films, series, animations). Unfortunately, there are some deep-rooted questions which are essential in qualitative research. therefore, some additional research questions were set:
— What brings people down to engage in quid pro quo attacks in Kazakhstan?
— What should be done in the country to make sure that people do not engage in quid pro quo social engineering attacks in Kazakhstan?
This brings to the following logical conclusion (responses to the research questions):
— In order to reduce the number of quid pro quo attacks, people in Kazakhstan should, certainly, develop their digital literacy, especially elderly people. This could be achieved by educating people certain courses, such as courses of critical thinking, digital literacy, or specialized courses for social engineering attacks.
— Another way of educating people is to teach them by providing lessons through media (cartoons, movies, stories, and even marketings). By using this method, it would a lot more effective to give people protection against quid pro quo attacks.
— However, there is also one unpopular, simple solution, which is stricter laws for frauds and those who engage in such attacks. Nevertheless, this method is considered as the least effective solution because it does not change the situation of the problem.
All things considered, increasing citizens' awareness of quid pro quo social engineering attacks could be achieved through the mentioned methods, all of which will ultimately improve the citizens' lives: they will reduce the risk of losing all personal information or money, stabilize the national economy, and encourage critical thinking among Kazakhs, teaching them how to handle similar situations.
Evaluation and further research
All things considered, the research succeeded in identifying the primary issues facing our city's society, along with their causes and potential remedies. There was main limitation during the research — a lack of responses, which made it challenging to gather information through auditory means and in order to mitigate this issue a link of the survey was sent by several various social medias to all parts of Kazakhstan. Though there is always space for improvement, suggested solutions can greatly help our society by raising awareness of quid pro quo attacks and how to prevent them. In the future, it is recommended to perform research with small target audience for more accurate and qualitative results. To learn more about this troublesome region of the nation, more research must be done. Initially, deeper motivations must be investigated of those who engaged in quid pro quo attacks as well as those who did not. In writing the results, also only the primary issues were emphasized; there are still a lot of unresolved issues.
Appendix
Informed consent form for to participate in the study
Research question: How to develop cybersecurity awareness among Kazakhstanis against quid pro quo attack?
Егер сіз сауалнаманың тілін ауыстырғыңыз келсе, жоғарыдағы батырма арқылы сізге керек тілді таңдай аласыз / Если вы хотите изменить язык опроса, вы можете сделать это, выбрав нужный язык с помощью кнопки выше / If you want to change the language of the survey, you can do it by selecting the needed language with the button above.
Description: You are invited to participate in a study aimed at determining the causes of the spread of the social engineering attack «quid pro quo» and ways to solve this problem.
A give-and-take exchange characterizes the quid pro quo attack. It means «something for something».
In the case of a service for a service, the promised benefit or advantage in exchange for information usually takes the form of a service. Let's say a bank employee contacted you and offered an interesting promotion for your account or credit card. But for this, he needs your username and password or the numbers on the front and back of the card. You provide him with this information without any discussion: in the end, you notice that all the financial savings on the card or in the electronic purse disappear. Quid pro quo attacks are based on manipulation and abuse of trust. As such, they fall under social engineering techniques such as phishing attacks (including point-phishing and whaling attacks), harassment, or the use of prepositions.
In this survey, you will be asked 9 questions regarding the causes of the spread of the quid pro quo attack and finding ways to prevent this problem. Please answer the questions honestly and feel free to express your opinion, because all your answers are important for this study.
Time involvement: Your participation will take approximately 5–6 minutes.
Anonymity and confidentiality procedures: The survey is anonymous. Your answers to those questions related to your personality and personal information will not be published or sent to other people to save your confidentiality.
Participant's rights: If you have read this form and have decided to participate in this project, please understand your participation is voluntary and you have the right to withdraw your consent or discontinue participation at any time without penalty. The alternative is to refrain from participating.
Contact information:
Questions: If you have any questions, concerns, or complaints about this research and its procedures, contact my GPPW teacher, Baizhanov Yeraly, baizhanov_e@akb.nis.edu.kz.
1. Please select options below if you agree to participate in this study and go to the next page.
Please select 5 options.
— I have carefully read the information provided.
— I have been given full information regarding the purpose and procedures of the study.
— I understand how the data collected will be used.
— I understand that I am free to withdraw from the study at any time without giving a reason.
— With full knowledge of all foregoing, I agree, of my own free will, to participate in this study.
References:
- Craigen, D. (2014). Defining cybersecurity . TIM Review. https://www.timreview.ca/article/835
- Creswell, J. W. (2001). Educational research: planning, conducting, and evaluating quantitative and qualitative research . http://ci.nii.ac.jp/ncid/BB26859968
- Dara Security. (2015, May). Quid pro quo: What is the cost of a free gift? — Dara Security. Dara Security — Security Assessments & Compliance. https://www.darasecurity.com/quid-pro-quo-whats-the-cost-of-a-free-gift/
- Dicih, Y. (2023, April 6). Banks warn Kazakhstanis about a new type of fraud . Orda. https://orda.kz/banki-preduprezhdayut-kazahstanczev-o-novom-vide-moshennichestva/
- FBI. (2019, April 25). BEC Cost Organizations US$1.2 Billion in 2018. TrendMicro. https://www.trendmicro.com/vinfo/de/security/news/cybercrime-and-digital-threats/ic3-bec-cost-organizations-us-1–2-billion-in-2018
- ForbesKz, Р. (2022, August 18). The level of digital literacy of the population in Kazakhstan has increased to 87 %. Forbes.kz. https://forbes.kz/news/newsid_282566
- ForbesKz, Р. (2022, August 18). Since the beginning of the year, scammers have called Kazakhstanis 44 million times. Forbes.kz. https://forbes.kz/news/newsid_319592
- Maulenkulov, М. (2023, May 10). This is definitely a scammer: how Kazakhstanis can identify calls from intruders. https://www.nur.kz/nurfin/personal/2019864-eto-tochno-moshennik-kak-kazahstantsam-vyyavit-zvonki-ot-zloumyshlennikov/
- Miller, E. (2023, April 4). Quid Pro No-Go: How to Avoid a Quid Pro Quo Social Engineering Attack. Social Engineering . https://b2a.kz/QxX
- Mitnick Security Consulting. (n.d.). The history of social engineering. https://www.mitnicksecurity.com/the-history-of-social-engineering
- Nadeem, M. S. (2023, December 20). Social engineering: Quid Pro Quo attacks . Mailfence Blog. https://blog.mailfence.com/quid-pro-quo-attacks/
- Jamesju. (2023, August 4). Quid pro quo social engineering [infographic and explanation]. Thomson Reuters Law Blog. https://legal.thomsonreuters.com/blog/quid-pro-quo-social-engineering-infographic-and-explanation/
- PurpleSec. (2023, February 22). 2023 Cyber Security Statistics: The ultimate list of stats, data & trends | PurpleSec. https://purplesec.us/resources/cyber-security-statistics/
- Raza, M. (2023, February 14). Social Engineering Attacks: The 4 stage Lifecycle & Common Techniques. Splunk-Blogs. https://www.splunk.com/en_us/blog/learn/social-engineering-attacks.html
- Ruzmatova, M. (2023, November 27). Fraudsters called Kazakhstanis 37 million times in 2023. el.kz. https://el.kz/ru/37-mln-raz-zvonili-moshenniki-kazahstantsam-v-2023-godu_98283/
- Techslang. (2021, March 12). What is a Quid Pro Quo Attack? Techslang — Tech Explained in Simple Terms. https://www.techslang.com/definition/what-is-a-quid-pro-quo-attack/
- Walden University. (2020). Strategies used to mitigate social engineering Attacks — ProQuest. https://b2a.kz/toA
- What are some of the advantages and disadvantages of using quantitative and qualitative data? (2023, May 18). https://b2a.kz/wUN

