This paper investigates some methods of cryptographic protection of information during its transmission over insecure channels. Our work reveals the principle of encryption using a decentralized key distribution as a way to transform the processed in information systems original data into a cryptogram or a ciphertext. The trend of modern cryptography development and the actual problems of end-to-end encryption in the information space are also considered.
Key words: cryptographic protection of information, end-to-end encryption, asymmetric algorithms, decentralized key distribution.
В данной работе исследуются методы криптографической защиты информации при её передаче по открытым каналам связи. Раскрывается принцип шифрования с использованием децентрализованного распределения ключей, как способ преобразования обрабатываемых в информационных системах исходных данных в криптограмму или шифртекст. Рассматриваются также тенденции развития современной криптографии и актуальные проблемы сквозного шифрования в информационном пространстве.
Ключевые слова: криптографическая защита информации, сквозное шифрование, криптографические алгоритмы, асимметричные алгоритмы, децентрализованное распределение ключей.
Nowadays, one of the most important missions of the state is to provide information security. In modern society information has become the resource number 1. Therefore, information flows must be protected by all means.
There are some cryptographic methods of information protection including encryption which are used for this purpose. Encryption is the process of transforming the unprotected public information (a plaintext) into the protected private one, i.e. a ciphertext or a cryptogram. Today, the most promising way of encryption is end-to-end encryption. It implies the use of a key, which is known only to the participants of this process.
The essence of end-to-end encryption (E2EE) is in the fact that it’s impossible to intercept the message during its transmission or reception. E2EE is especially common for Internet communication, it is used by such applications as WhatsApp, Viber, Skype and Telegram.
In establishing communication between the two workstations, two keys are generated at each workstation: public and private (secret). The secret key is designed to decrypt the received information and it never leaves the local device, while the public key is transmitted through the open channel from the sender to the recipient. Only the sender can encrypt the message with his public key and the decryption is available only for the receiver who has a private key. In this case there is no loss of data.
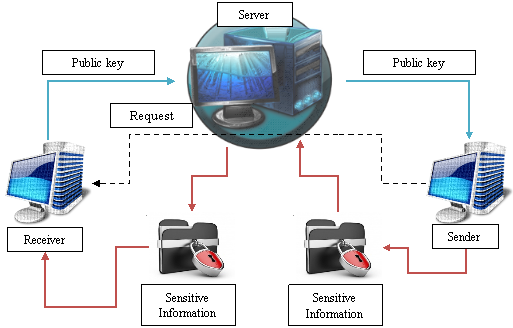
Fig. 1. The information transfer system with the decentralized key distribution
The communication system using the decentralized key distribution has a number of problems. The first problem is the loss of restricted information during its storage. It means that the information is protected only during its sending, while the receiving and sending points can be attacked. Thus, users of infocommunication networks, where E2EE is used, may be at risk.
The next problem is authorization of users who are the participants of the communication process. The problem of gaining access to private information consists of a process of authorizing users. Subscriber`s telephone number through SMS-message is used for authorization. This method of data transmission is based on SS7 (Signaling System # 7) technology, which was developed 40 years ago and according to the modern standards has weak security parameters. Thus, cryptanalysts have the ability to access information transfer devices and then directly access the information.
It is proposed to implement the principle of usage of conditional entropy in SS7 technology. However, it means to achieve an appropriate degree of uncertainty not by distortion of information by noise but by influencing information at some statistical element. As a result, secure authentication will be provided for a key and SMS-message. It should be borne in mind that the routing of the confirming data must be done through the channels that the servers provide.
It is necessary to add that in the current political situation in our country, such an encryption algorithm may be a threat to the information security of the Russian Federation. The Islamic state (IGIL, a terrorist organization banned in Russia) recruits the soldiers, using messengers (including Telegram) with end-to-end encryption. These means of communication can’t be intercepted or hacked.
This problem can be solved at the legislative level in the Russian Federation. Another solution of this problem is to provide access to the intelligence information processed in such information systems.
Thus, we can conclude that the uncontrolled usage of messaging by end-to-end data encryption poses a direct threat to the national security of the Russian Federation. Messenger creators believe that the secrecy of correspondence should be supported in full, but the problem is that terrorists can use it.
People do not understand that such free communication provides terrorists with the opportunity to secretly exchange data at all stages of training, including both the recruitment and the training of the recruits. Consequently, the structures that ensure security must control the Internet information.
References:
- Yo. Yazev. «Professional investigation. As enciphering in WhatsApp, iMessage and others», works 2016. [Electronic resource] — the access mode: https://www.iphones.ru/iNotes/595634 (Date of the address: 09/17/2017)
- Information portal «The Illustrated Self-instruction Manual on Information Security». [Electronic resource] — the access mode: http://samoychiteli.ru/document34384.html (Date of the address: 09/22/2017)
- Information Roem.ru portal, 2017 [Electronic resource] — the access mode: https://roem.ru/04–04–2017/246777/telegram-vs-isis/ (Date of the address: 10/10/2017)
- R. Rozhkov, S. Goryashko. «The State Duma asks FSB to block Telegram», 2015. [Electronic resource] — the access mode: https://www.kommersant.ru/doc/2855366 (Date of the address: 10/13/2017)

