In this paper is given Security parameters and requirements of database management system. At the end of the paper is analyzed MSAccess, SQL Server and Oracle DBMS.
Keywords: DBMS, security, security model, comparing DBMS.
Evaluation of DBMS (database management systems) is an important point of information technologies. However, easier said than done, performance evaluation of database system is a non-trivial activity, made more complicated by the existence of different flavors of database systems fine-tuned for serving specific requirements. However, performance analysis tries to identify certain key aspects generally desired of all database systems and try to define benchmarks for them. In the rest of this survey, we shall provide a formal definition of database systems followed by few methods to categorize or classify database systems. This shall be followed by a look at the various performance evaluation techniques that are employed to benchmark database systems, some of the key benchmarking techniques used in practice in the industry and some open source benchmarking schemes available for use in the public domain [1].
A database security manager is the most important asset to maintaining and securing sensitive data within an organization. Database security managers are required to multitask and juggle a variety of headaches that accompany the maintenance of a secure database.
If you own a business, it is important to understand some of the database security problems that occur within an organization and how to avoid them. If you understand the how, where, and why of database security you can prevent future problems from occurring.
Having a perfectly fitting database management system (DBMS) is a key component for today’s business success. The DBMS manages the interaction between your applications and the underlying database. It assures that the correct data is available for the requested user group when needed. When choosing a DBMS from the variety of concepts and vendors, you should consider the following points before making a decision [2].
- Data Model. For a long time, the relational concept was dominant, however recently NoSQL databases have again become more successful.
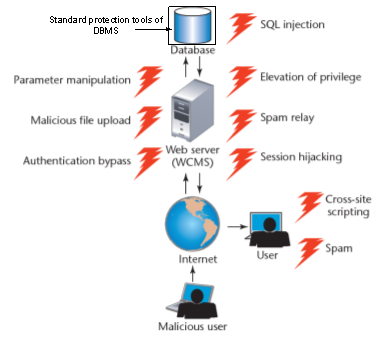
Fig. 1. Security in database management system
- Data Consistency. Nowadays, collecting data is not a big effort anymore. But, keeping the data consistent becomes even more important as more sources feed into the database.
- Data Security. For most companies, data availability is a key business success factor and should always be guaranteed. The ability to backup and restore the databases is essential and needs to be possible with your chosen DBMS.
- Data Protection. Access protection and encryption should allow protection of personal data. Every DBMS provide different methods of protect the data through encryption, but the possibility to define routines and access rights is different for every system.
- Multi Access and Integration. Setting up a DBMS, running it and extending it for future growth, requires enough flexibility to allow integration into the given IT infrastructure.
- Efficiency backup. When we talk about the efficiency of DBMS, we usually mean the response time. You will find on premise and cloud solutions available on the market.
- Usability. Different user groups will be working with the DBMS. There are the administrators, IT and Database admins, application integrators and data consumers.
- Implementation and Service Costs. The modifiability and availability of support and documentation needs to be taken into consideration as part of the implementation and Total Cost of Ownership (TCO). Also, several measures to ensure database security are given below:
Elimination of vulnerabilities—continually assess, identification and remediation of vulnerabilities that expose the database.
Isolation of sensitive databases—maintainance an accurate inventory of all databases deployed across the enterprise and identification of all sensitive data residing on those databases.
Enforcement of the least privileges—identification of user entitlements and enforcement of user access controls and privileges to limit access to only the minimum data required for employees to do their jobs.
Auditing for deviations—implementation of appropriate policies and monitor any vulnerabilities that cannot be remediated for any activity the deviating from authorized activity.
Response to the suspicious behavior—alert and response to any abnormal or suspicious behavior in real time to minimize risk of attack.
The main results of comparing DBMS (Access, SQL Server and Oracle) (table 1) are given here. The security level of DBMS is shown in following table and it is indicated that oracle is the best one among three DBMS.
Table 1
Main results of comparing DBMS
|
DBMS Methods |
MS Access |
SQL Server |
Oracle |
|
Access |
By user and group |
By three command |
By four command |
|
Role |
No |
Server and Database Level |
By set_role commands |
|
Encryption |
With password |
TDE |
TDE |
|
Authentication |
No |
Windows and SQL Server authentication |
Simple and proxy authentication |
|
Grouping |
Users group |
Administrator, database owner and users group |
Administrator, database owner and users group |
|
Backup |
Manual |
Parallel (back up to 32 devices at once) |
Parallel |
|
Audit |
No |
By security log, application log and file |
Audit vault |
|
Fire-Wall |
No |
No |
Three motion |
|
Cloud |
No |
Amazon EC2 |
In version 12c |
References:
- Sumathi S., Esakkirajan S. Fundamentals of relational database management systems. — Springer, 2007. — Т. 47.
- Singh S., Rai R. K. A Review Report on Security Threats on Database //International Journal of Computer Science and Information Technologies. — 2014. — Т. 5. — №. 3. — С. 3215–3219.
- https://www.testronix.com.ph/2018/01/30/8-key-considerations-choosing-dbms/
- https://blog.paessler.com/key-considerations-when-choosing-a-dbms

