This article is devoted to application of new methods and methods cyber criminalistics. Problems of cybercrime are considered in this article and given new methods.
Key words: cyber, criminalistics, cybercrime
We live in the information space. I can not say exactly how this information closer to reality or engage in fraud on the Internet, hacking passwords in large company sites or e-mail to threaten a person's life on the Internet, engage in hacking and other place around us every second growing cybercrime. What is cybercrime, and when there was this term in the Criminal Code. Computer security experts are well aware of the term and know what kinds of threats are struggling against them and define the concept of cybercrime [1,3].
Cybercrime- crimes are committed by people using information technologies for criminal purposes. In foreign countries, particularly the United States, have become widespread fraud related to the sale of domain names made a mass mailing e-mail messages in which, for example, the report attempts to unknown people register domain names similar to addresses belonging to the recipients and site owners are invited to register unnecessary their domain name to get ahead of these people. So, shortly after the attacks of September 11, 2001 US Federal Trade Commission said the fact the mass sale of domain names zone «USA». These groups of infringements are special part of the institution of criminal law the responsibility for these acts can not accommodate the Criminal Code of the Republic of Uzbekistan. As an independent institution for the first time is not isolated and requires special adopted article which refers to sub institute «Crimes against public safety and public order». Kinds of objects are considered crimes of public relations related to security of information and information processing systems by a computer.
Cybercrime information are: illegal access to computer information, creation, use and distribution of malicious computer programs [2,4].
Violation of the rights of information and unauthorized access to data remains sometimes a mystery, about the concept of cybercrime identified which is studied science Cybercrime happening crime with information technology. Fighting to cybercrime requires international co-operation, etc. This law is adopted by Council of Europe Convention on Cybercrime.
Council of Europe Convention on Cybercrime divides into four groups:
‒ The first group of offenses against the confidentiality, integrity and availability of computer data and systems are: illegal access (Art. 2), illegal interception (v. 3), the impact on computer data (wrongful intentional damage, deletion, deterioration, alteration or suppression of computer data) (Art. 4) or the system (Art. 5). Also in this group of crimes include illegal use of special technical devices (v. 6) — software designed or adapted for the commission of offenses set forth in Art. 2–5, as well as computer passwords, access codes, their analogues, by which can be accessed by the computer system as a whole or some part in there). In Art. 6 rates apply only if the use of (distribution) of special technical devices aimed at the commission of unlawful acts.
‒ The second group consists of crimes are associated with the use of computer tools. These include fraud, forgery and use of computer technologies (Art. 7–8). Forgery using computer technology includes malicious and unlawful entry, modification, deletion or suppression of computer data, entailing inauthentic data with the intent that it be considered or acted upon for legal purposes as authentic.
‒ The third group of production (for distribution through a computer system), supply and (or) provision for the use, distribution and purchase of child pornography and possession of child pornography in a computer memory (v. 9).
‒ The fourth group consists of offenses related to infringements of copyright and related to rights.
Under the Convention, each of the State Party is required to create the necessary legal conditions for the provision of the following rights and duties of the competent authorities to combat cybercrime: seizure of a computer system or part of the carrier; manufacturing and confiscation of copies of computer data; ensure the integrity and preservation of stored computer data relating to the case; destruction or suppression of computer data in a computer system.
The Convention also requires the necessary legal conditions in touch of Internet providers to collect and to fix or intercept the information you need with the help of available technology and promote the law enforcement agencies. It is recommended to oblige providers to maintain absolute confidentiality about the facts of this cooperation.
In early 2002, is admitted to Protocol № 1 of the Convention on Cybercrime, which adds to the list of crimes of dissemination of racist and other nature, inciting to violence, hatred or discrimination against a person or group of people based on the racial, ethnic, religious or ethnic affiliation.
The next step interaction with the subject is a subject of authentication. Authentication of the subject — is the subject of authentication with the ID. The authentication procedure determines whether the subject what himself declared [4,5].
After identification and authentication of the subject of the authorization procedure is performed. Under the threat of information security in computer network (COP) to understand an event or action that may cause a change in the functioning of the COP related to violation of protection of the processed information in it. Vulnerability information — is the possibility of such a state in which the conditions for the implementation of information security threats [4,5].
The attack on the Constitutional Court referred to the action taken by the infringer, which is to search for and use of a particular vulnerability. In other words, an attack on the COP is the implementation of information security threats in it.
Problems are arising from the security information transmission when the computer networks can be divided into three main types:
‒ interception of information — data integrity is preserved, but her privacy violated;
‒ modification of information — the original message is changed or completely replaced by others, and sent to the addressee;
‒ substitution of the authorship information. This problem can have serious consequences.
The specifics of computer networks, in terms of their vulnerability, mainly associated with the presence of an intense information exchange between geographically dispersed and diverse (heterogeneous) elements.
Vulnerable are literally all the main structural and functional elements of the Computer System: workstations, servers (Host-machine), bridging (gateways, switching centers), communication channels, etc. A large number of diverse security threat information from various sources [4,5]. In literature there are many different classifications, where the dividing criteria used types of dangers posed by the degree of malice, source of the threats, etc. One of the most basic classifications is shown in Fig. 1.
Natural threat — the threat is caused by exposure to the elements of the COP and its objective physical or natural processes of nature, beyond the control of man.
Artificial threat — a threat to the COP caused by human activity. Among them, based on the motivation of actions can be distinguished:
‒ unintended (inadvertent, accidental) threats caused by errors in the design of the COP and its components, software errors, errors in the actions of personnel, etc.;
‒ deliberate (intentional) threats associated with selfish aspirations of the people (hackers).
According to international standard GOSTR ISO / IEC 17799–2005, the information security policy should establish the responsibility of management, as well as to present the organization's approach to managing information security [4,5]. In accordance with this standard requires that the information security policy of the enterprise as a minimum, include:
‒ definition of information security, its overall objectives and scope, as well as disclosure of the importance of security as a tool that provides the ability to share information;
‒ presentation of the purposes and principles of information security formulated by the leadership;
‒ summary of the most important for the organization of security policies, guidelines, rules and regulations, such as:
‒ comply with legal requirements and contractual obligations;
‒ requirements for security training;
‒ prevention and detection of viruses and other malicious software;
‒ business continuity management;
‒ responsibility for violations of security policy.
‒ definition of general and specific obligations of employees in the management of information security, including information on incidents of violation of information security;
‒ links to documents that complement the information security policy, for example, more detailed policies and procedures for specific information systems, as well as the safety rules are followed by users.
Information Security Policy of the company must be approved by management, published and communicated to all employees in an accessible and understandable form [3].
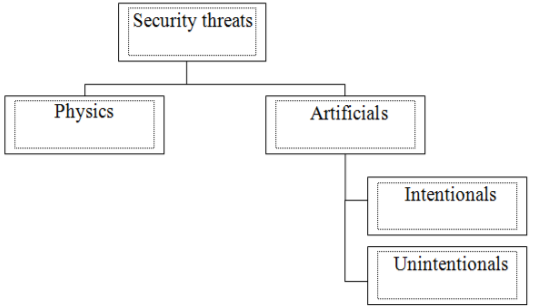
Fig.1. General classification of security threats.
References:
- The Council of Europe Convention-11.12.2008, www.coe.int
- Fundamentals of Information Security. Textbook for high schools / EB Belov, VP Moose, RV Meshcheryakov AA Shelupanov. -M.: 2006–544
- Vikhorev SV Kobtsev RY How to determine the sources of threats? // Open systems № 7–8 / 2002. http://www.elvis.ru/files/howto.pdf.

