One of the most important areas in the field of information security research is to detect intrusions. Currently, there are many ways of detecting cyber attack of various types. Among them, always emphasizes the ways that allow you to detect attacks previously unknown species. To detect such attacks usually applied, the approach based on the identification of abnormal behavior in the network. Often it invited to use various heuristics to identify clearly different from normal behavior. In particular, we propose a heuristic based on the assumption that a legitimate user is not to contact him for an unknown object on the network. To use this heuristic should be placed in a network system that do not participate in other industrial processes, and not advertised as a working network services — the so-called decoy targets. Any network activity is a false target is suspicious and should consider as malicious.
The network model, containing the decoy targets. A distinctive feature of this heuristic is that its effectiveness depends on the proportion of the total number of attacks attributable to the decoy targets. In turn, it is determined by the ratio of the number of false targets and real network and their other parameters. Let us consider the model to associate with the required efficiency parameters of false and real goals.
The basic concept of this model is the notion of purpose. Under the aim will be to understand the working on the host in the network process, performing a certain code. So how often network attacks aimed at vulnerabilities in the operation of the application software, a sense of purpose can be considered reasonable. Attack in this model will be called the following steps performed by the attacker:
− select according to some rule targets for the next attack;
− checking that the appropriate target vulnerabilities;
− attempt to exploit the vulnerabilities.
As a rule, any attack is focused on a set of code vulnerabilities. Thus, it makes sense to group goals in classes on the basis of his matches (![]() in Figure 1). Each class will contain both real and false targets.
in Figure 1). Each class will contain both real and false targets.
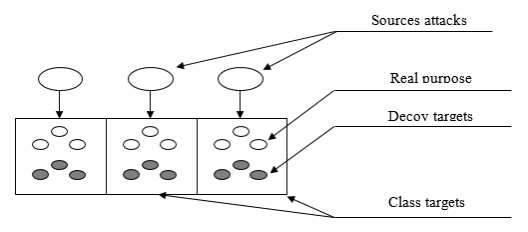
Fig. 1. The scheme of interaction model components
It is believed that the attackers represented by a number of copies of malicious software, each of which carries out cyclically attempts to attack on the network. Attempts attacks occur at discrete points in time. One can assume the presence of a large number of independent sources of attacks at each time point. Consequently, we can consider the total flux attacks from these sources, considering it simple [1]. Obviously, in conditions of changing characteristics of the external environment will change and the parameters recorded flow attacks, but it assumes that it is always possible to choose a period of time during which the flow can be considered as the simplest. In this case, it suffices to consider the state of the environment at discrete points in time intervals corresponding stationary parameters of detected attack flow. At the same time the state itself will be determined by the parameters of these flows, and the impact on the protected network attacker can be described as a set of independent streams of attacks, one for each class of targets.
Consider the probability of an attack on any false target in the network in each gap flow stationary parameter attacks. Due imposed definitions and assumptions, this probability is equal to the sum of the probabilities for all classes of targets. It has the following expression for this probability [2]:
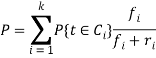 (1)
(1)
where ![]() is the probability of selecting the next step of the target
is the probability of selecting the next step of the target ![]() and
and ![]() classes the number of decoy targets and real purpose, according in
classes the number of decoy targets and real purpose, according in ![]() class and the number of
class and the number of ![]() class goals.
class goals.
The probability of selecting targets from a particular class in practice can be determined as the ratio of the average number of attacks on the purpose of the class to the total of all attacks on the network end. These average values can be defined using the notion of intensity ![]() flow attacks. The best in terms of the proposed model will be such a configuration parameter of the decoy targets in network, which will provide the maximum value of
flow attacks. The best in terms of the proposed model will be such a configuration parameter of the decoy targets in network, which will provide the maximum value of ![]() with set limits on the number of decoy targets in each class. This is true for the fixed time.
with set limits on the number of decoy targets in each class. This is true for the fixed time.
Now suppose that the intensity of the attack effects for each class objectives change over time. If one calculates the optimum configuration of the decoy targets at each step of excluding previous changes, there is a danger that some of the decoy targets in network is embedded in a small time ago, will be removed in the next step. Obviously, this does not give them to fulfill their function and can potentially lead to their disclosure. Thus, considering the dynamics of the model, it is necessary to take into account this important goal setting, as the time elapsed from the moment of its appearance, or the availability of time. Each class can be characterized by the distribution uptime availabilities goals of this class. It is possible to formulate the following limitation: time allocation available of decoy targets should not be different from the distribution of the timing of availability of RC in the same class. This restriction follows directly from the fundamental principle of the introduction of false objects in the network: to the attacker failed to disclose the fact of its misinformation, false as the object must be less different from actual.
Another limitation associated with this same principle is the need to maintain a stable set of services that are on the same host in the implementation of decoys. Furthermore, there is usually a restriction on the maximum number of hosts — «carrier» decoys. Thus, it is possible to list the following options purposes, in terms of influencing the accepted model the effectiveness of heuristic:
− belonging to a class goal from the point of view of the coincidence of executable code;
− belonging to the class of real targets or decoy targets;
− time when the target became available in the network;
− host, which is the goal.
For the network as a whole are calculated parameters such as:
− the number of classes on the basis of goals matches the executable code;
− distribution target available time in each class;
− the number of real and false targets in each class, as well as the maximum possible number of hosts that carry decoys.
Formally, the model can be written as follows, taking into account:
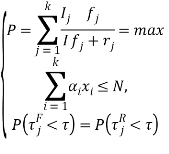 (2)
(2)
where ![]() number of targets classes in the network;
number of targets classes in the network; ![]() intensity of attacks on targets
intensity of attacks on targets ![]() class;
class; ![]() intensively attacks on targets all classes;
intensively attacks on targets all classes; ![]() fixed set of target types from the set of all available configurations on the network;
fixed set of target types from the set of all available configurations on the network; ![]() number of hosts with decoys corresponding
number of hosts with decoys corresponding ![]() configuration;
configuration; ![]() maximum number of hosts with decoys;
maximum number of hosts with decoys; ![]() and
and ![]() time availability of false and real purposes, respectively.
time availability of false and real purposes, respectively.
The method of determining the optimum parameters of decoy targets. In whole, the method involves iteratively performing the following steps:
- Getting the model input parameters and initial configuration of the decoy targets.
- The calculation of the optimal configuration of the decoy targets with solving the optimization problem defined by the model.
- Among the possible control actions are selected such that provide maximal increase the probability of selecting an attacking of decoy targets.
- Under change the parameters of the model the optimal configuration to be calculated again.
Development of intrusion detection model based on the provisions of the security policy
Intrusion detection system widely used as one of the most popular remedies modern automated information system (AIS). The increasing complexity of the technology of computer attacks, observed at the moment, requires the detection of the most dangerous attack complex, consisting of several stages, during which the attacker carries out malicious acts using various methods. Thus, computer attacks should be viewed as attempts to violate security policy (SP) in the protected AIS, and for them to identify the necessary means to control many different parameters AIS.
Detection of complex attacks is difficult because of the need to analyze different sources of information and research the relationship between the identified simple attacks. Intrusion detection system should be available to the database attributes identified ontology attacks. For intrusion detection inappropriate allocation of common features, common to all AIS as generally intension attacks varies for each AIS because it depends on the characteristics of the system to which the attack is directed. In particular, the formation of detecting signs must be taken into account especially the objectives, structure and functioning of the AIS. As a basis for the formation of signs of detection of computer attacks can be used AIS. SP allows for features and characteristics of AIS, in particular, describes a model of insider and external threats. It also includes external AIS information — model of external threats, as well as information about the role of AIS in the outside world [3].
The structure includes private SP, describing the parameters and criteria for the security of protected classes of AIS resources. These policies define, that is an anomaly and normal behavior for a variety of system and network settings and contain an assessment of critical deviations from normal behavior scenarios. Thus, the SP can provide the information necessary for the formation of signs detect attacks based on simple features of AIS. However, SP is a document and contains almost no quantitative characteristics of different criteria and parameters.
Thus, in achieving the objectives of the study have any problem formalization signs of intrusion detection, derived from the provisions of the positions SP, and the development of the algorithm, which allows detect complex attacks based on these signs. Also is investigated the possibility of using set of fuzzy variables and fuzzy rules for solving this problem. Let the private security policy states that users should not use the AIS resources during off-hours. Therefore, the presence of a certain number of people are outside working hours should refer to the possibility of penetration in the AIS. The simultaneous presence of a large number of active users should signal the penetration of the AIS and the possibility of the spread of the attack phase. In turn recorded the fact of penetration in turn suggests that the level of risk for AIS great. In addition, the monitoring policy may indicate the need for analysis of monitoring files at least once every three days. This deviation from the monitoring policy at a high possibility of the spread of the attack must also point out that the level of risk for AIS is very high. For formalized description of the above provisions of SP advisable to write them in the form of the following rules:
![]() : if the users of the system «more» and the «outside», the possibility of the penetration of the «big»;
: if the users of the system «more» and the «outside», the possibility of the penetration of the «big»;
![]() : if the users of the system «a lot», the possibility of the penetration of the «big» and the possibility of extending the «high» of attack;
: if the users of the system «a lot», the possibility of the penetration of the «big» and the possibility of extending the «high» of attack;
![]() : if the time elapsed since the last analysis monitoring «significant» files, the violation of policy monitoring «great»;
: if the time elapsed since the last analysis monitoring «significant» files, the violation of policy monitoring «great»;
![]() : if the possibility of the penetration of the «big», the risk level of «high»;
: if the possibility of the penetration of the «big», the risk level of «high»;
![]() : if the possibility of the spread of the attack «big» and a violation of the «big» monitoring policy, the level of risk is «very high».
: if the possibility of the spread of the attack «big» and a violation of the «big» monitoring policy, the level of risk is «very high».
In general, the premise and the conclusion of the rule can consist of any non-zero number of atomic formulas of the various logical operations. Model rules of the example shown in Figure 2.
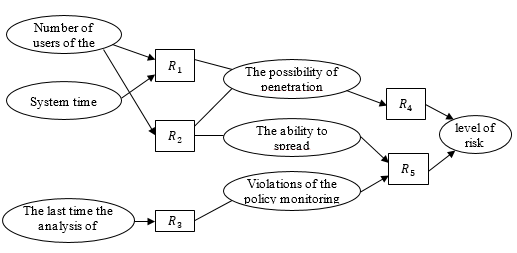
Fig. 2. Model rules, that interpreting the positions of the SP
For formalizing, the positions of the SP proposed to use fuzzy hierarchical construct. In accordance with the use of fuzzy sets it allows you to formally define vague and open-ended terms that justifies the use of fuzzy sets and fuzzy logic for the formalization of the SP provisions and to detect deviations from normal behavior AIS. In the above snippet rules model, interpreting the SP position, used linguistic variables «number of users of the system», «system time», «the ability to penetrate», «the possibility of extending», «risk» and the other taking the different values of the form a «big» and «high». In this case, the input values are the variables «number of users of the system», «system time», «the last analysis of monitoring files». Other values are obtained by computing for data fuzzy rules.
References:
- Gulomov Sh. R, Kadirov M. M. Guidelines for testing intrusion detection systems. Transactions of the International scientific conference «Perspectives for the development of information technologies ITPA-2015» 4–5 November, Tashkent 2015.
- Gulomov Sh. R., Kadirov M. M., Tulyaganov Z. Ya. The methodology of the ways for increasing the efficiency of intrusion detection systems. International Journal of Engineering Innovation & Research Volume 5, Issue 5, ISSN: 2277–5668, 2016, India, 296–302.
- Makarenko S. I. Information security. Textbook for university students. Stavropol, 2009. 372 p.

